How do subscriptions fare in a recession?
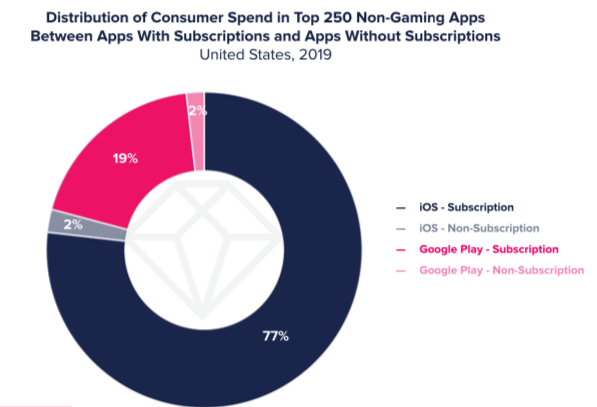
Source: App Annie, State of Mobile 2020 The subscription model (‘subscription economy’ was a term apparently coined at least four years ago) is becoming de rigeur in many zones. App Annie’s recent State of Mobile report found that In App subscriptions contributed to 96% of spend in the top non-gaming apps. As an overall proportion … Read more